Unveiling the Secrets of Wireless Network Hacking: A Comprehensive Guide for Beginners

In the ever-evolving digital landscape, cybersecurity has become paramount. With the proliferation of wireless networks, the need for proficient hacking skills has skyrocketed. This guidebook, "Complete Guide To Learning The Basic Of Cybersecurity Wireless Network Hacking," empowers beginners with the knowledge and techniques to delve into this fascinating domain.
Chapter 1: Cybersecurity Fundamentals and Ethical Hacking
Embark on a journey into the basics of cybersecurity, exploring key concepts like network security, threat mitigation, and ethical hacking. Understand the principles of responsible and legal hacking practices, ensuring your knowledge is used for constructive purposes.
5 out of 5
| Language | : | English |
| File size | : | 2422 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 323 pages |
| Lending | : | Enabled |

Chapter 2: Wireless Network Architecture and Security
Uncover the intricacies of wireless network architecture, including components like access points, routers, and antennas. Delve into the security mechanisms employed to protect these networks, such as encryption, authentication, and intrusion detection systems.
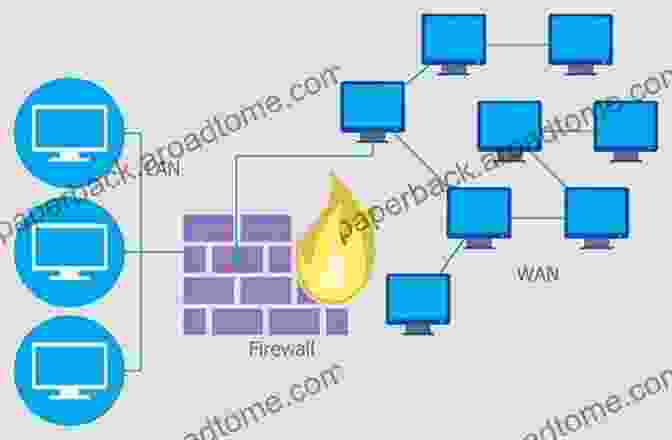
Chapter 3: Reconnaissance and Vulnerability Assessment
Step into the world of reconnaissance, where you'll learn to gather information about target networks effectively. Discover techniques for identifying potential vulnerabilities and weaknesses, paving the way for successful exploits.
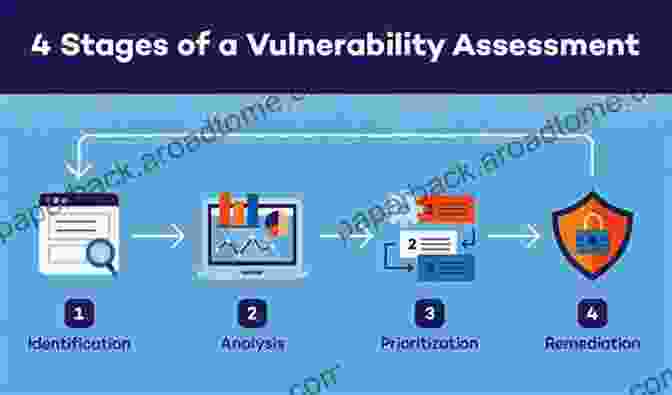
Chapter 4: Penetration Testing and Wireless Attacks
Equip yourself with practical penetration testing strategies, utilizing tools like Wireshark and Nmap to uncover network vulnerabilities. Explore various wireless attacks, including deauthentication attacks, man-in-the-middle attacks, and rogue access point attacks.

Chapter 5: Password Cracking and Sniffing
Master the art of password cracking, employing password cracking tools like Hashcat and John the Ripper. Learn about network sniffing techniques, enabling you to capture and analyze network traffic for sensitive information.

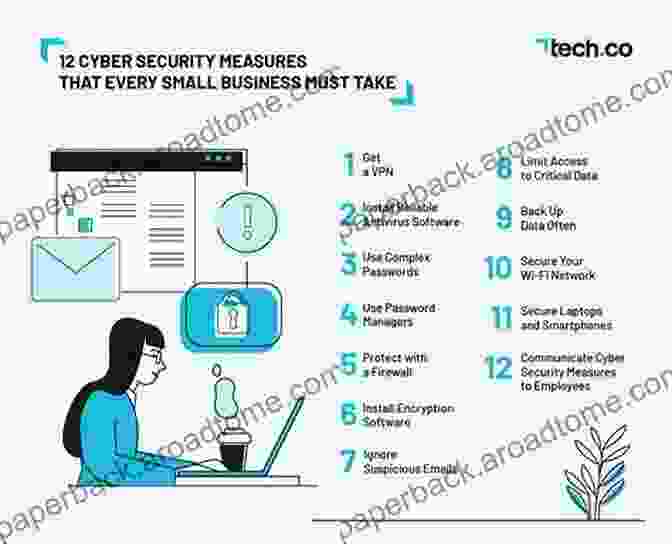
Chapter 6: Wireless Security Measures and Best Practices
Safeguard your wireless networks by implementing robust security measures. Discover best practices for configuring firewalls, enabling strong encryption, and implementing intrusion prevention systems.
Chapter 7: Legal Aspects and Ethical Considerations
comprendere the legal implications and ethical considerations associated with wireless network hacking. Adhere to responsible hacking practices, ensuring your actions comply with applicable laws and regulations.

This comprehensive guidebook empowers you with a solid foundation in cybersecurity and wireless network hacking. By harnessing the techniques and knowledge within these pages, you can effectively protect your networks, uncover vulnerabilities, and navigate the ethical landscape of hacking. Remember, knowledge is power, and responsible use of hacking skills is crucial for a secure and interconnected digital world.
5 out of 5
| Language | : | English |
| File size | : | 2422 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 323 pages |
| Lending | : | Enabled |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Hayden MitchellUnveiling the Enchanting Landscapes of Yorkshire Dales: A Journey Through...
Hayden MitchellUnveiling the Enchanting Landscapes of Yorkshire Dales: A Journey Through... Winston HayesFollow ·5.8k
Winston HayesFollow ·5.8k Dwight BellFollow ·18.4k
Dwight BellFollow ·18.4k Lucas ReedFollow ·12k
Lucas ReedFollow ·12k Roald DahlFollow ·9.6k
Roald DahlFollow ·9.6k Shane BlairFollow ·18.7k
Shane BlairFollow ·18.7k Jesse BellFollow ·15.7k
Jesse BellFollow ·15.7k Christian BarnesFollow ·3.4k
Christian BarnesFollow ·3.4k Eric NelsonFollow ·10.7k
Eric NelsonFollow ·10.7k

 Isaiah Powell
Isaiah PowellWisconsin Clinic Pilots Mobile Crisis Response System For...
MADISON, Wis. - A new mobile crisis...

 Daniel Knight
Daniel KnightUnleash Your Creativity: A Masterclass in Fabulous Nail...
Embellish Your Fingertips with Captivating...

 Clark Campbell
Clark CampbellDetect When You Are Being Emotionally Manipulated By...
Emotional manipulation is a subtle but...

 Eli Brooks
Eli BrooksNeurological Disorders Papers: Dissociative Identity...
What is Dissociative...

 Ricky Bell
Ricky BellAn Introduction to Islam for Jews: Unveiling the Tapestry...
A Bridge of Understanding: Exploring Islam for...

 Octavio Paz
Octavio PazAchieving Longevity: The Complete Step-by-Step Guide to...
**** In the ever-evolving landscape of health...
5 out of 5
| Language | : | English |
| File size | : | 2422 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 323 pages |
| Lending | : | Enabled |